One Card to Rule Them All
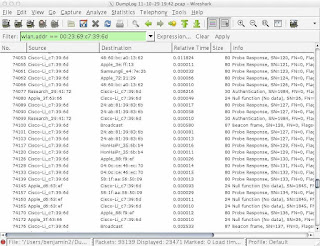
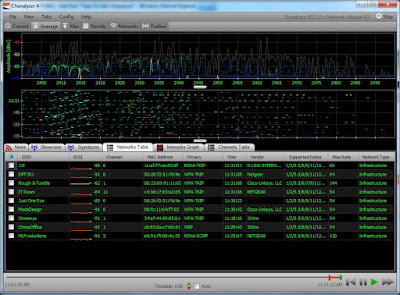
FINALLY! If you do a lot of sniffing, there is a chance that you have a bag full of USB adapters whose contents look like this: Riverbed AirPcap NX Metageek WiSpy DBx D-Link DWA-160 Cisco-Linksys WUSB600Nv1 D-Link DWL-122 D-Link DWL-G122 Ubiquiti SR71-USB (w/ two HG2401RD-MMCX 2.4 GHz antennas) I do, and it stinks . AirPcap is for Wireshark, WiSpy is for Chanalyzer, the DWA-160 and SR71-USB are for AirMagnet software, the DWL adapters are for Kismac and the Cisco-Linksys is for OmniPeek. It is a bit frustrating, especially if I need to switch between applications. Well, today I am a happy(er) man. The screen in that shot is WildPackets OmniPeek, running like a champ. And do you see that little thing on the right, there? That is the D-Link DWA-160, working with OmniPeek like a champ. It is a little thing, I guess, but I am very happy to be able to use the DWA-160 adapter with WildPackets OmniPeek. This means that Fluke Networks' Air...