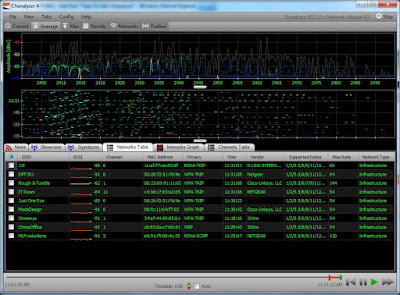
And a one, and a four, and a eight, and a 'leven...
Channel choices can be a tricky thing, especially in the 2.4 GHz frequency band. I saw a network recently that had an unconventional channel design, but the network seemed to work pretty well. Channel selection has long been a peculiar topic for 2.4 GHz WiFi networks. Per-channel frequency allocations in the band are 5 MHz wide (enough for a cordless phone or PowerPoint clicker, for example), but transmissions are much wider. The exact amount of bandwidth taken up by WiFi devices varies depending on the standards supported (802.11 b, g or n), the radio's transmission power and possibly other mysterious factors as well. (Just try running a spectrum analyzer around gear that supports transmit beamforming (TxBF) and you'll see what I mean.) A seasoned rule of thumb has been to keep APs running on channels 1, 6 and 11 in an environment that supports ubiquitous coverage. The theory is that, at typical transmission/antenna configurations, WiFi devices will transmit over bandw...