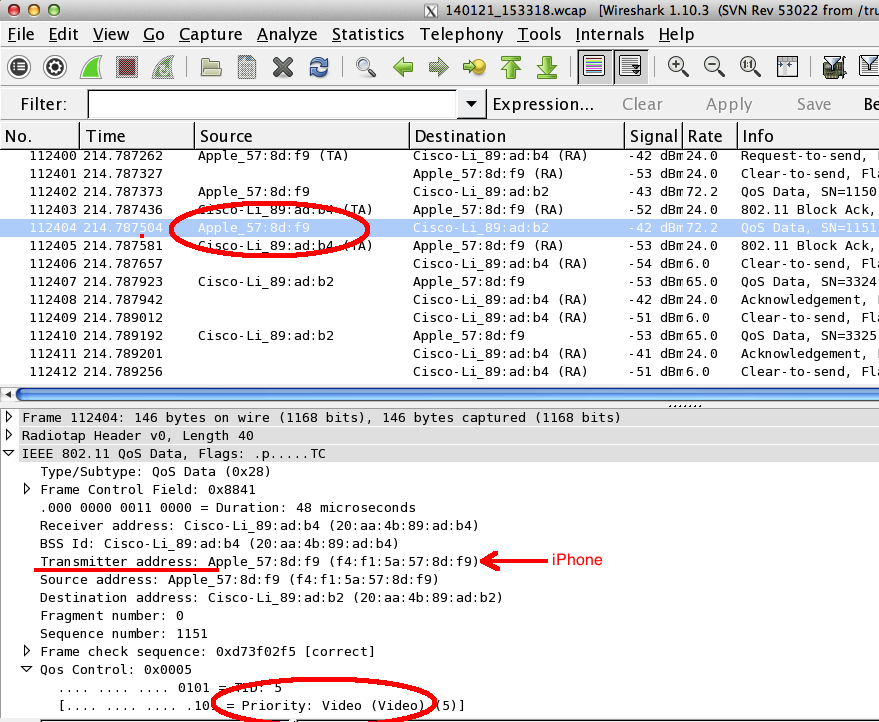
Why Are You Speeding Up My Wi-Fi Calling, Apple? (It Might Make Things Worse)

It's summer in Los Angeles, which can only mean one thing: Sequels! As movie fans indulge in a third 'Avengers', a fifth 'Jurassic Park', and what feels like a seven hundreth 'Star Wars', this here blog is providing a sequel to a probably-long-forgotten Sniff Wi-Fi post called ' Why Are You Slowing Down My Wi-Fi, Apple? ' Turn down the lights, pop some popcorn, and enjoy the twists and turns of this harrowing look into Wi-Fi Calling on iPhones. Several months ago, this blog highlighted the Wi-Fi behavior of the iPhone X using OmniPeek. Truth be told, that post was a little bit like the latest 'Spider-Man' sequel: attention-grabbing title, some interesting content, but ultimately nothing consequential. And just as movie fans knew that Michael Keaton's flying bird character wasn't going to beat the lead superhero, a lot of Wi-Fi folks already knew that Apple iOS devices use Protection (called a "TXOP" in the blog po...